Public sector security professionals are very optimistic about the impact generative AI could have on their operations and security, though security teams located in the Asia-Pacific region will need to battle more than their fair share of incoming cyber threats on their way to realising AI’s full potential.
The 2024 State of Security report from cybersecurity and observability leader Splunk found public sector security teams are the most likely to see opportunities for generative AI, with 55% of these respondents saying it would have a ‘game-changing’ impact, compared with 47% across all industries surveyed.
However, Splunk’s report, which surveyed 1650 security executives globally, painted a harrowing picture of a region under cyber siege. Australian respondents collectively said they were experiencing a higher than average volume of every attack type, including a large number of state-sponsored attacks.
Singapore is also dealing with high attack volumes. The Cyber Security Agency (CSA) of Singapore’s 2023 Cybersecurity Health Report, which surveyed over 2000 businesses of all sizes in 2023, found that 8 in 10 experienced a cyber incident in the last year, with about half encountering attacks several times a year.

“A core aim of public sector organisations around the world, including in the Asia-Pacific region, is to maintain and build the trust that their citizens place in them, and ultimately to safeguard national security,” said Robert Pizzari, Splunk’s Group Vice President Strategic Advisor.
“It is to be expected that public sector agencies in regional technology hubs like Australia and Singapore would look to the potential of generative AI to assist with capabilities like threat detection in order to be able to prevent serious breaches, which continues to be absolutely paramount.”
Public sector awake to the cybersecurity potential of generative AI
Public sector organisations worldwide are very positive about the benefits generative AI will bring for cybersecurity teams. Splunk found 55% of respondents thought generative AI would end up being more beneficial to security defenders than threat actors, compared with 46% across all industries.
Public sector respondents were also more likely to envision security use cases for AI such as:
- Threat detection (46%, versus 35% across all industries)
- Penetration testing (42%, versus 29% across industries)
- Security team training (44% versus 34% across industries)
Public sector respondents also had greater SecOps automation aspirations than their peers, which included automating SSL certificate management (43% versus 31% across industries), the orchestration of actions across security controls (53% versus 38%) and alert enrichment (47% versus 32%).
Public sector leading the development of AI usage policies
Security teams in the public sector have also been fast to adopt practical measures to deal with the emergence of AI tools. The State of Security Report found 77% of security teams in the public sector had already adopted acceptable use policies for AI, compared with just 66% across all industries.
Australia’s 2023-2030 Cyber Security Strategy and Singapore’s National AI Strategy 2.0, which both address the security implications of AI, are best practice regional examples of the public sector moving to ensure citizens will be able to take advantage of safe, responsible and secure AI into the future.
APAC region faces a high attack volume from global threat actors
Public sector organisations in the Asia-Pacific are facing up to very high attack volumes in the region.
According to research from non-profit Financial Services Information Sharing and Analysis Centre, one in 20 APAC organisations were hit with ransomware between January to October 2023, and the region recorded a 15% year-over-year increase in cyberattacks during the first nine months of the year.
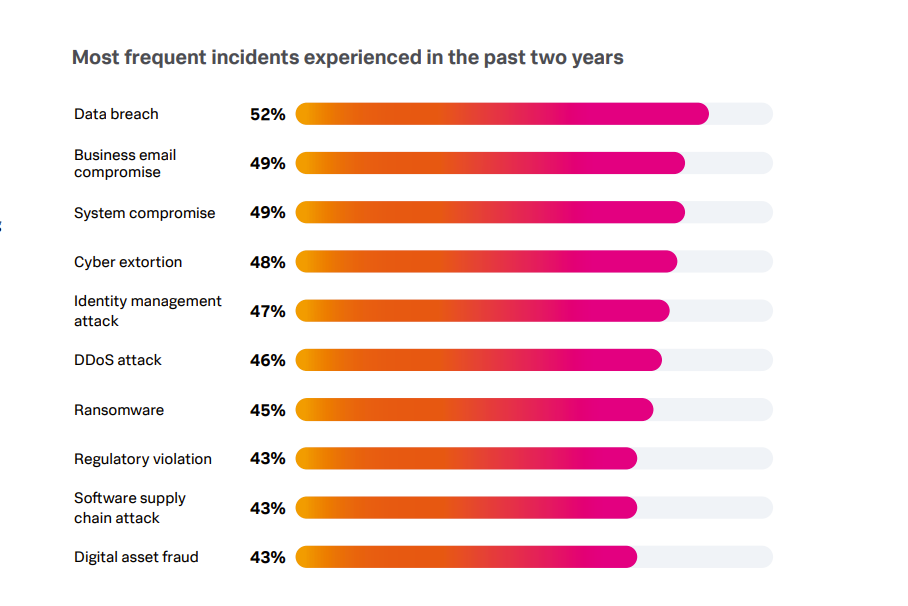
Splunk found organisations in Australia, for example, are facing more attacks than elsewhere: 63% had experienced a data breach, compared with 52% globally, 55% had seen an insider attack, compared with 42% around the world, and 59% had been hit by business email compromise, versus 49% globally.
Australia was also more concerned with state-sponsored attacks. Fifty-six percent of Australian respondents experienced nation-state attacks, compared to 39% globally, and 44% organisations strongly agreed geopolitical stress was exacerbating cyberattacks, compared with 29% globally.
Singapore’s CSA found 99% of attacks in Singapore resulted in a business impact, with disruption (48%), data loss (46%) and reputational damage (43%) experienced the most. Ransomware, social engineering scams and exploitation of cloud misconfiguration were Singapore’s top attack categories.
Many victims in the region also admit to paying ransoms. Splunk’s 2023 CISO Report, which surveyed CISOs around the world, found 83% of respondents had paid attackers if they were hit with a ransomware attack, with more than half paying at least US$100,000.
The public sector is combating cyber threats but is also being attacked
The public sector is responding. For example in July 2023, the Association of Southeast Asian Nations officially opened a joint cyber security information sharing and research centre, called the Cybersecurity and Information Centre of Excellence, to boost the region’s shared cyber threat defences.
When the public sector itself is attacked, system misconfigurations are a top vector for threats, with 42% of global respondents saying they are most often the root cause. Public sector respondents are also more concerned about the lateral movement of threat actors, with 39% listing this as a primary concern.
The Asia-Pacific’s regional challenges include observability and cyber security maturity
Splunk’s research found top cybersecurity challenges differ by country. For example, observability is an outsized problem for Australian cybersecurity professionals, while in Singapore, cybersecurity maturity was found to be lagging the high levels of digitisation and connectedness seen across its economy.
In Australia, 72% of respondents said they were pivoting too much between disparate security tools, compared with 43% in other global markets, while 35% of Australian respondents surveyed cited issues with visibility across their attack surface, compared with just 20% globally.
“It’s not surprising this is translating into a slower mean time to detection; 50% of Australian respondents told us the typical MTTD takes months, compared to 19% globally. There is an overall challenge of too many tools, which can make it more difficult to detect a problem,” Pizzari said.
Singapore has the highest percentage of respondents who identified their cybersecurity programs as ‘developing’ (14%, compared to 7% globally), and are less likely to say they have the authority and resources to address cybersecurity challenges (only 77%, compared to 91% in aggregate).
They are also the least likely (28%) to report a significant rise in anticipated cybersecurity spending, and are less likely to recognise the business impact of digital resilience; for example, only 23% strongly agreed digital resilience could improve customer retention, compared to 33% globally.
Awareness key to realising AI’s public sector potential
Australia is one APAC nation that has set a whole of government zero trust target for 2030. Splunk’s research suggests the public sector is in a good position to utilise AI more broadly in the region, for everything from improved threat and fraud detection to streamlining compliance and reporting.
To do this, the region will need to build cybersecurity skills. In Singapore, the CSA found knowledge and experience is the top barrier to cyber security implementations, while in Australia, 52% of security team members had led projects multiple times without requisite experience, versus 39% globally.
But AI could help here too, by bridging the cyber skills gap. “Because of the cyber skills crisis, there is now a challenge to do more with less, and the public sector needs the same cyber security skills as the private sector. Utilising generative AI could help supplement those skills needs,” Pizzari said.
Public sector should capitalise on thirst for AI knowledge
The public sector is doing well with learning. Splunk’s survey found respondents place more focus on security awareness training (24%, compared to 17% across industries), though they see a higher lack of cybersecurity knowledge and commitment from executives (28%, compared to 20% across industries).
Pizzari said that, following their lead in developing AI regulation and policy, including the acceptable use of AI, public sector agencies in the Asia-Pacific could combine their enthusiasm for the potential of AI with learning and awareness across their workforces, to enhance their preparedness towards 2030.
“Awareness is critical within the public sector; there are a lot of resources, but there’s a challenge around how they get the right type of enablement and education out to staff around how best to use AI technology or how they can potentially use it to innovate in the environment,” Pizzari explained.
With insights contributed by Harry Chichadjian, FSI & Industry Advisory Lead, APAC and Nathan Smith, Head of Security, APAC.
Access Splunk’s 2024 State of Security report.

